Blog
Phishing Scams: The New Wave of “Social Engineering”
October 19, 2022
Massachusetts residents have received text messages and emails that include a link requesting claimants enter their login and password on a site that looks similar to UI Online. If you have received such a message, please do not respond.
 This can be critical information to relay to your employees – especially anyone who may have been furloughed or collected unemployment throughout the COVID pandemic given the myriad relief programs funded by the Federal government and administered through unemployment insurance. Of course, these phishing scams are not new – in March of last year, the US Secret Service warned of similar scams, with a similar scam was reported in Indiana earlier this year.
This can be critical information to relay to your employees – especially anyone who may have been furloughed or collected unemployment throughout the COVID pandemic given the myriad relief programs funded by the Federal government and administered through unemployment insurance. Of course, these phishing scams are not new – in March of last year, the US Secret Service warned of similar scams, with a similar scam was reported in Indiana earlier this year.
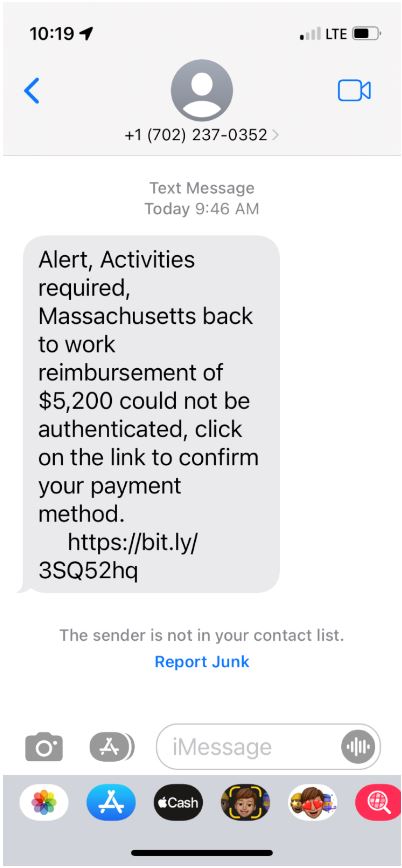
One message reads: “Alert, Activities required, Massachusetts back to work reimbursement of $5,200 could not be authenticated, click on the link to confirm your payment method.” With a shortened URL via bitly. The link takes the recipient to a website that on the surface appears to be a Massachusetts Department of Unemployment Insurance (DETMA) website., but on further inspection, it lives on a Wix domain.
Of note here, there is no “Back to Work Reimbursement” of $5200 or other amount. Earlier this year, Massachusetts created a “HireNow” program to encourage employers with $4000 per eligible hire, but that was money paid directly to employers, not employees. In December 2021, Governor Baker signed the COVID-19 Essential Employee Premium Pay program, from which $500 payments were delivered to nearly 240,000 people in March a first round of the program, with a second round in June. In no permutation of these payments though were there $5200 being made directly to recipients.
This is an example of a “Social Engineering” phishing attack, where scammers try to use psychological manipulation to create situations where unsuspecting users divulge sensitive information in the service of either receiving some perceived benefit, or simply by pleasing another person. Rather than an attacker searching for a software vulnerability to exploit, cybercriminals can gain access to systems, data or physical spaces by creating trust or other influence.
There are a variety of social engineering tactics, phishing scams target a victim via email, telephone or text message by posing as a real figure to convince victims to disclose sensitive data. In this case it’s a social security number and possibly a DET password.
Social engineering and cyber-security training is a proactive way to help keep your company secure and employees avoid these scams. Reach out to CIP HR Services to discuss resources.